
Network sandboxes are an underrated yet powerful cybersecurity tool. Much like virtual machines isolate malware, network sandboxes safely analyze suspicious files before they reach a user’s system. By executing potential threats in a controlled environment, they help detect and block malware without risking real systems. Network sandboxes are isolated environments used to safely test potentially malicious files over network traffic without affecting the rest of your system.
We all know what virtual machines are and what they do. But if you don’t, think of them like emulators—except
instead of running a game like Kingdom Hearts on a PS2 emulator, a virtual machine (VM) emulates an entire
operating system on your computer.
Using software like VirtualBox, you can load an .iso file of an OS—Ubuntu, Debian, Windows XP, etc.—and run it
inside your main system. You also get full control over resources, deciding how much storage, memory, and CPU
power the VM can use.
A common cybersecurity use case for virtual machines (VMs) is malware analysis—testing, reverse-engineering,
and studying malware in a controlled environment. The reason? You definitely don’t want to run malware on your
personal computer.
Now, can malware escape a virtual machine? Technically no, but in rare cases, yes.
Malware cannot break out of a VM on its own—it requires an exploit. For example, if you have a shared folder between
your VM and host machine, malware could use it to squeeze through and escape. Otherwise, if your VM gets infected,
you can simply shut it down or restore a clean snapshot, leaving your main system unharmed. More information about
the likelihood of malware escaping your VM can be found
here.
However do not take it as professional advice, as it is from an infosec forum.
Now, apply that same logic to network security. If a network service detects suspicious activity—say, a
potentially harmful file download—it can sandbox the file inside an isolated "virtual machine" environment.
If the file turns out to be malicious, the service closes, preventing the malware from ever reaching the actual
system. This is what a network sandbox does.
A network sandbox is an isolated testing environment that allows security teams to observe, analyze, detect,
and block suspicious activity on a network. It serves as an additional layer of defense against previously
unknown attack vectors. By running potentially malicious files in a controlled, segregated environment that
mimics a real operating system, security teams can conduct advanced malware analysis without risking the
integrity of the actual network.1
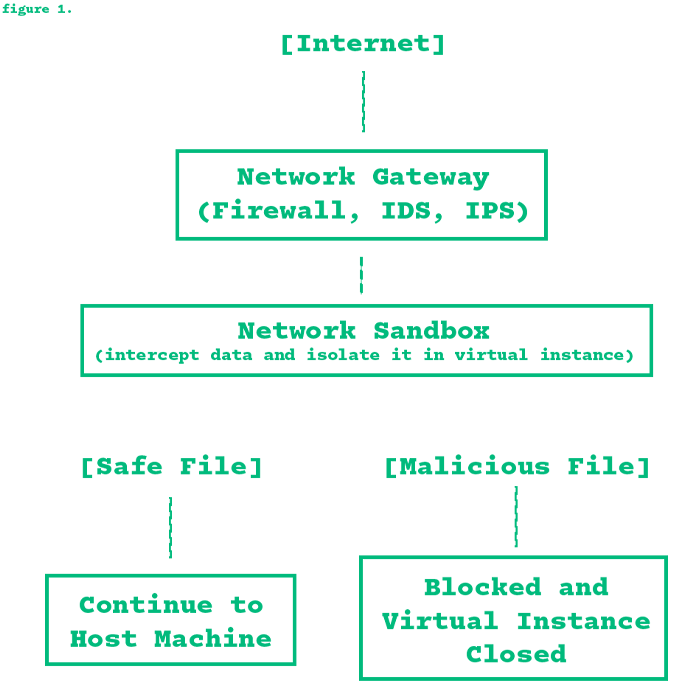
A user downloads a file from the internet. This could be an email attachment, a software installer, or any other type of file.
Before the file reaches the user’s device, the data is intercepted by a network security gateway. A network security gateway is a device that acts as the entry point to a network, filtering and inspecting all incoming and outgoing traffic. Examples can be a firewalls, IDS, or IPS.2
A firewall sets the boundaries for network traffic, blocking or allowing data based on predetermined protocols. An IDS watches over network activities, flagging any irregularities for review, without directly affecting data flow. An IPS plays an assertive role, not just detecting, but also preventing identified threats from compromising the network.
The file data is then redirected and sent to a network sandbox, which then executes an isolated virtual environment designed to safely run and analyze files. The sandbox monitors the file’s behavior, checking for signs of malware, such as suspicious system modifications, network connections to malicious servers, or attempts to alter files or processes.3
If the file behaves normally, it’s flagged as safe and continues to the main system. If the file behaves maliciously, it blocks it from reaching the user. On top of blocking the file, a network sandbox also creates reports on its malicious activity and can take measures to alert the security team, log details about the threat, or send the malware to cybersecurity researchers for further analysis. 4
Even if the malware tries to execute harmful actions inside the sandbox, it remains contained because the sandbox is isolated from the real system. Once analysis is complete, the sandbox environment is reset or deleted, ensuring that no traces of the malware persist.
Several security tools leverage network sandboxing to detect and analyze threats before they reach a user’s system. These tools execute suspicious files in isolated environments, observing their behavior to determine if they are malicious. Here are some notable network sandboxing technologies:
Cuckoo Sandbox
A Cuckoo Sandbox is a free and open-source application that allows malware to be launched in a safe and isolated environment. The concept is that the sandbox tricks the virus into believing it has infected a real host. After that, the sandbox will log the malware's activities and provide a report detailing the things the virus tried to accomplish in this safe setting. 5
VMRay Analyzer
Uses hypervisor-based monitoring for advanced malware detection without modifying the analyzed sample. VMRay allows security teams to filter out the noise and respond to the real malware threats faster. Contextual threat intelligence provided by VMRay Analyzer also allows you to start automated threat hunting in seconds. 6
FireEye Malware Analysis
An independent malware sandbox engine that enables files and URLs to be submitted for explosion within the virtual environment. It can identify whether the submitted file or URL is malicious by using certain behavioral and statistical analysis. 7
Checkpoint Sandblast
Uses sandboxing to prevent zero-day attacks before they reach endpoints. Utilizing a combination of threat emulation, AI engines, and threat extraction, it essentially acts as a preemptive defense against unknown malware and exploits, including phishing, social engineering, and ransomware, before they can enter a network or reach users. 8
Crowdstrike Falcon Sandbox
an automated malware analysis tool that uses a sophisticated sandbox environment to deeply analyze suspicious files, including unknown and evasive threats, to identify malicious 9
These technologies play a crucial role in modern cybersecurity, allowing security teams to preemptively neutralize threats before they can compromise a network.
Network sandboxing is a powerful yet often overlooked cybersecurity tool. Similar to how virtual machines contain malware in a controlled environment, network sandboxes isolate and analyze suspicious files before they reach a system. By acting as a proactive defense layer, they help security teams detect and neutralize threats before they can cause harm. Despite their effectiveness, network sandboxes don’t receive as much attention as traditional security measures like firewalls and antivirus software. Hopfully you've learned a few things about network sandboxing and how it helps protect a network.