Qubes OS is a security-focused operating system that isolates applications and tasks into separate virtual machines (qubes) to contain potential threats. It supports multiple operating systems, uses a template system for efficient updates, and allows for disposable qubes that self-destruct upon closure. With features like Whonix integration for anonymity, device isolation to prevent hardware attacks, Split GPG for secure key management, and CTAP Proxy for safer two-factor authentication, Qubes OS offers a highly compartmentalized and secure computing environment.
Out of all the operating systems out there that claim to be safe and secure against all types of attacks, Qubes OS just might be the most secure.
Qubes OS is a free and open-source operating system. It achieves its security by implementing compartmentalization, the division of something
into sections or categories. This operating system does quite literally that, divides its software and applications into separates processes.
It uses virtualization to create and manage isolated compartments, known as “qubes”, each operating in a different virtual machine.
Qubes OS basically runs each instance of a program in its own virtual machine (VM). For example, if you open a web browser, it
launches within a dedicated VM. Opening another instance of the same browser creates an entirely separate VM, completely
separate from the other web browser.
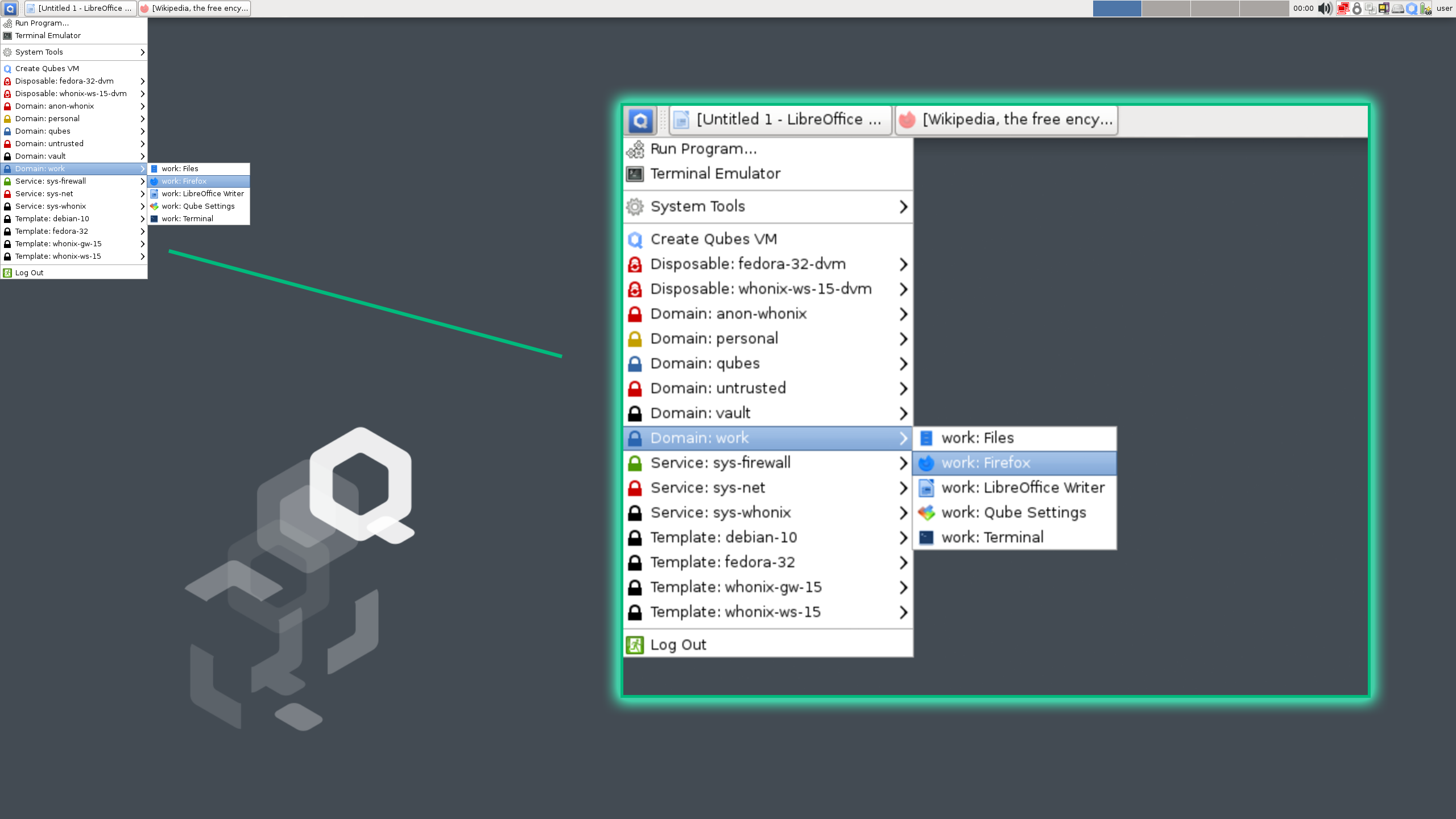
The interesting thing about the OS is if you need to manage multiple virtual environments efficiently, it categorizes VMs based on their purpose.
You can designate specific VMs for different aspects of your digital life, such as a "Work" browser for professional tasks and a "Personal" browser
for private use. Each category operates independently, preventing data leaks and cross-contamination between activities.
This compartmentalization extends beyond browsers to applications like email clients, messaging apps, and document editors,
providing a secure and organized computing experience.1
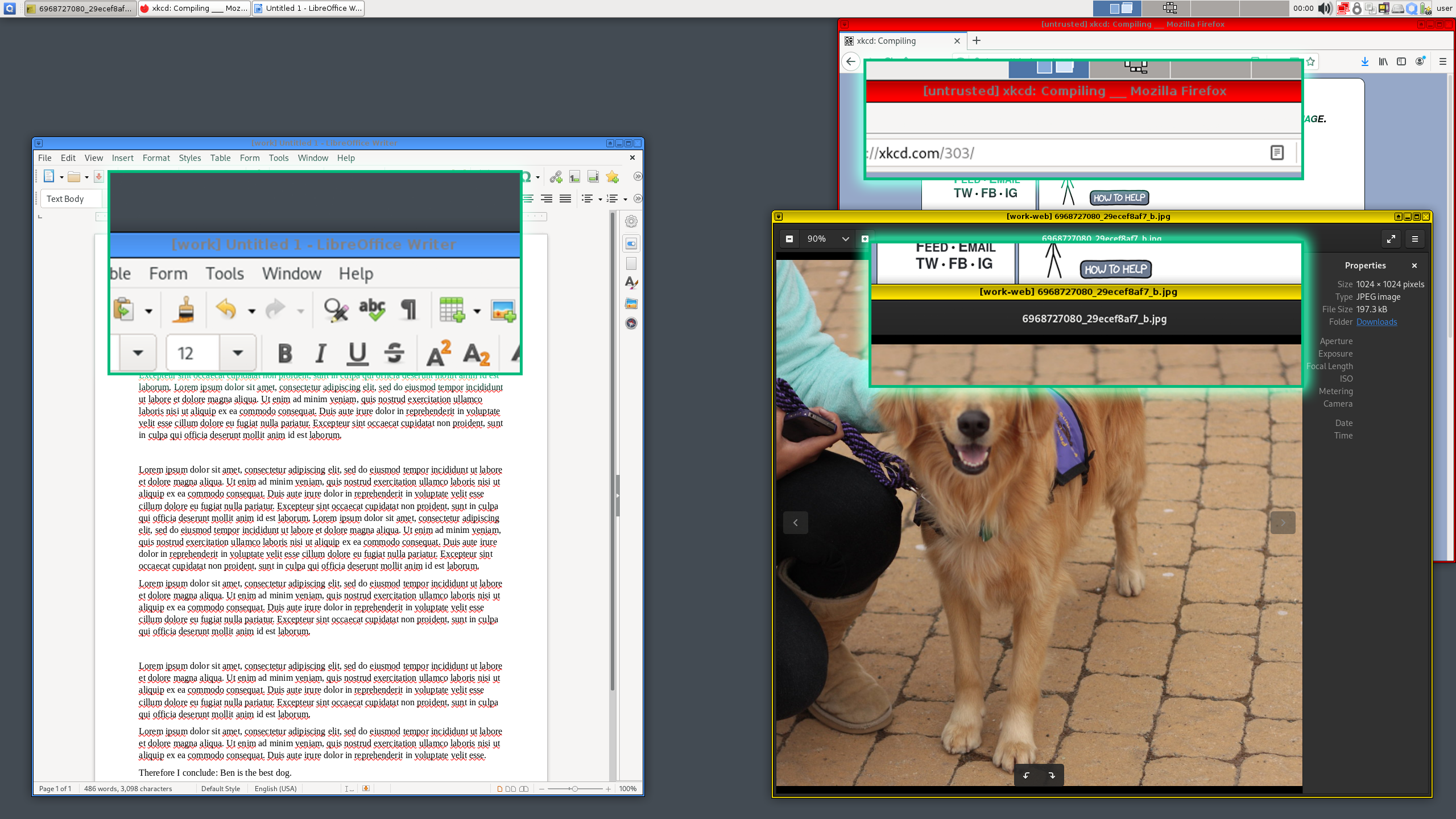
"In this example, the word processor runs in the “work” domain, which has been assigned the “blue” label. It is fully isolated from other domains, such as the “untrusted” domain (assigned the “red” label – “Watch out!”, “Danger!”) used for random Web browsing, news reading, as well as from the “work-web” domain (assigned the “yellow” label), which is used for work-related Web browsing that is not security critical. Apps from different domains run in different AppVMs and have different X servers, filesystems, etc. Notice the different color frames (labels) and VM names in the titlebars. These are drawn by the trusted Window Manager running in Dom0, and apps running in domains cannot fake them."
QubesOS runs with the assumption that your application will be compromised. So, the idea of total virtualization helps in a situation where if an application or VM gets exposed and compromises, you or the OS can simply shut it down, and then start a whole new VM application, as if nothing happened. Nothing else is infected either because the VM’s having no connection or contact with each other. Qubes OS provides an advanced infrastructure for programming inter-VM services, such as a PDF converter for untrusted files (which is described in this article). It even provides a dedicated firewall that itself runs in an isolated Firewall VM.
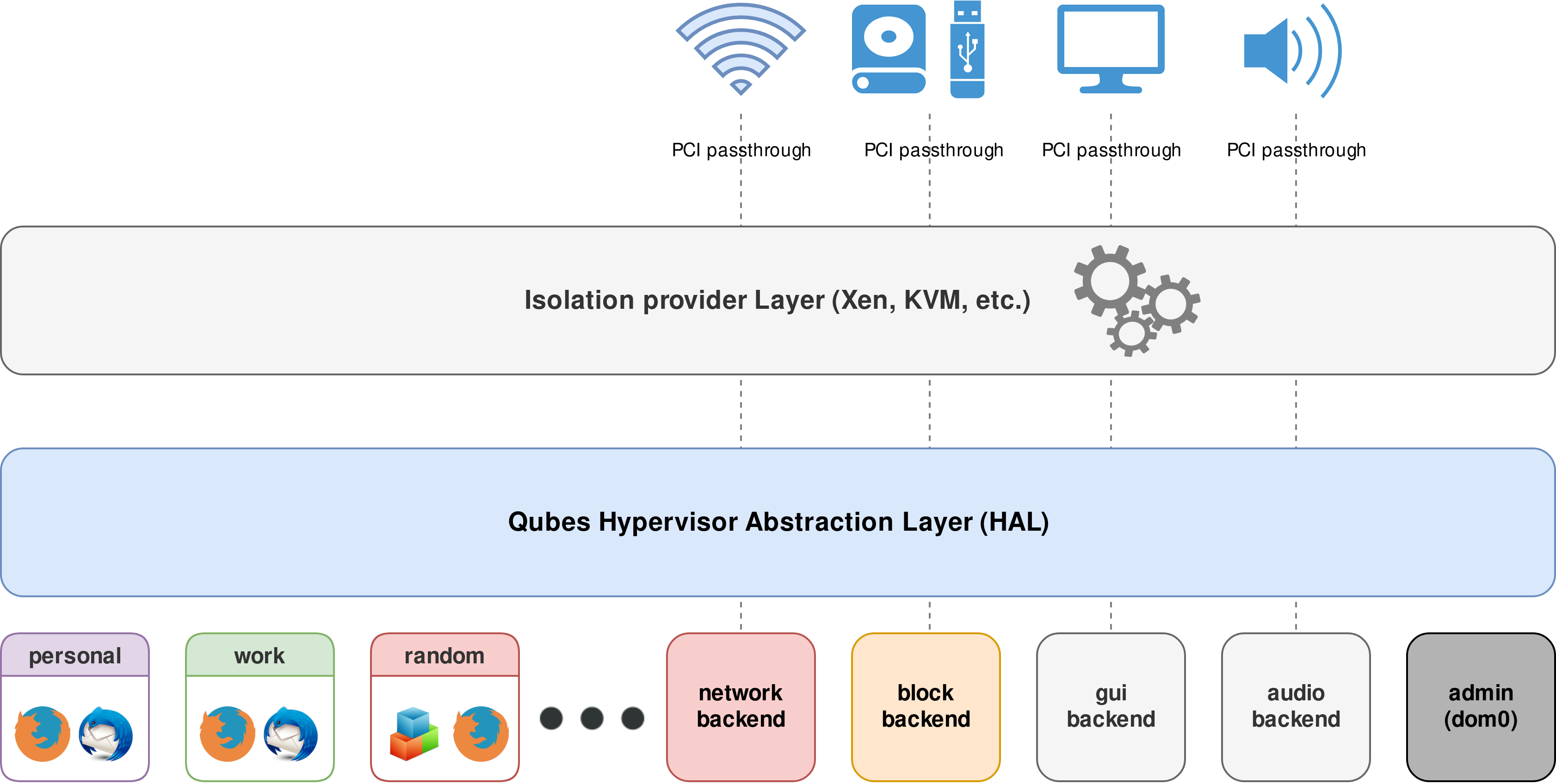
Qubes lets the user define many secure compartments known as qubes, which are implemented as lightweight virtual machines (VMs). For example, the user can have “personal,” “work,” “shopping,” “bank,” and “random” app qubes and can use the applications within those qubes just as if they were executing on the local machine. At the same time, however, these applications are well isolated from each other. Qubes also supports secure copy-and-paste and file sharing between qubes, of course. 2
You can run various operating systems concurrently, including Fedora, Debian, and Windows, within each VM application. The OS also supports disposable qubes that self-destruct upon shutdown, which can be ideal for handling untrusted content. Say you get infected, you can just shut it down like nothing happened. For enhanced privacy, Qubes OS integrates with Whonix, routing network traffic through the Tor network. Device isolation further strengthens security by isolating network cards and USB controllers, mitigating hardware-level attacks. Additional features like Split GPG protect private keys by keeping them separate from the domains where they are used, while the CTAP Proxy enables secure two-factor authentication without exposing the web browser to the full USB stack.3
QubesOS deploys the Xen Hypervisor to allow all its virtualization. Xen is able to create and manage the multiple VM’s a user creates.
And as just a quick side note, a hypervisor is a computer software that allows an operating system to actually achieve virtualization.
Windows uses Microsoft’s own hypervisor to allow users to use virtual machines, and MacOS has its own hypervisor.
4
Its architecture can be described with 3 distinctive layers. It starts off with Dom0 (Domain Zero, or Administrative Domain).
This privileged domain has direct access to the hardware and is responsible for managing the graphical user interface (GUI) and
coordinating other qubes. To minimize security risks, Dom0 is intentionally isolated from network access. Dom0 is the first domain
that boots and manages the Xen host, including other virtual machines.
5
The next two are the App Qubes (Application Domains) and the Serive Qubes. The App Qubes are user-created VMs designated for specific tasks or applications,
such as personal browsing, work-related activities, or financial transactions. Each App Qube operates independently, ensuring that a compromise in one does not
affect others. The Service Qubes are dedicated to handling specific system services like networking and USB device management, these qubes further isolate critical
functionalities from the user environment.
Some key architecture features include:
In terms of security, Qubes OS does stand out. The technology it uses is really outstanding and the premise of having multiple
virtual machines running different and completely seperate processes is really interesting. It runs on the assumption that you
can and most certainly will be compromised. And if you do, it's okay because Qubes OS knows what to do.
This is an OS I heavily recommend to be used, not only just to play around with, but also as a solid operating system to work on.
Download and try out Qubes OS in your VM,
https://www.qubes-os.org/downloads/